Introduction
Let’s be honest – the blame doesn’t always lie solely with the perpetrators of cyber attacks like ransomware. In this personal account, I’ll share a story that exposed my ignorance, leading to a devastating data disaster and straining a precious friendship. Join me as I recount how a seemingly small oversight in data security had far-reaching consequences and the valuable lessons it taught me about safeguarding sensitive information.
The Genesis of the Project
In 2018, my friend approached me with an opportunity to modernize their invoicing process by transitioning from an Excel-based system to a web-based solution. Excitedly, I took on the project as my second contract, collaborating with an excellent Software Engineer friend to build the system. We opted for the PEAN stack – Angular, NodeJS/ExpressJS, and PostgreSQL – an impressive choice for our needs.
After months of hard work, the system was up and running smoothly. Although I encountered the challenge of finding affordable and reliable servers while living in South Africa, I managed to secure a low-spec Windows Server in the US. Despite some minor adjustments and fixes, the system performed flawlessly, making everyone involved quite pleased.
The Fateful Incident
While on a relaxing vacation, I received a shocking call from my friend, informing me that the website was down on a critical day when they needed to print a large invoice for a client. My investigation revealed that all databases had vanished, replaced with a placeholder email demanding a ransom for their return.
The Ransom Dilemma
Unwilling to comply with the attacker’s demands, I decided to restore the databases from my backups. But to my dismay, the backups had been failing for quite some time, and I hadn’t noticed. The realization left me with no other option but to confront the attacker directly.
The Ransom Negotiation
In a polite email exchange, the attacker demanded a ransom payment in Bitcoin for the return of my databases.

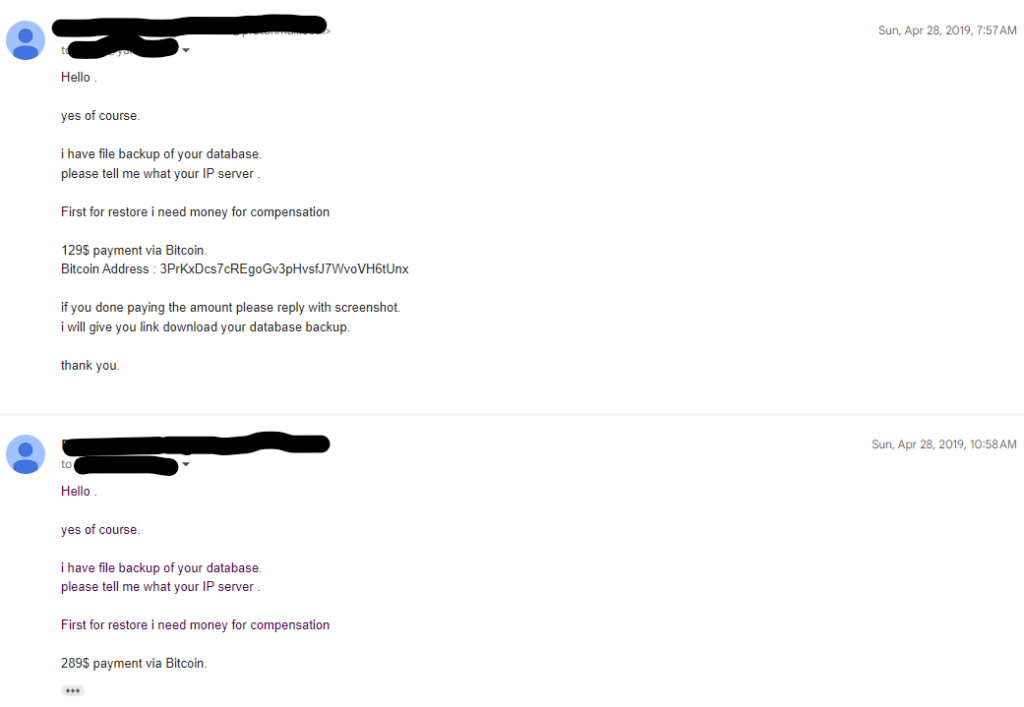
As much as I wished to retrieve the lost data, I couldn’t risk paying without any guarantees. With a Rand/Dollar exchange rate of R14 to $1 hit was simply too much money at that time. In addition, having read of cases where victims were left empty-handed despite paying, I had found myself without a solution and had to face the music.
Facing the Consequences
Sadly, I had to admit to my friend that the critical data for their invoice was lost, resulting in a sense of embarrassment and unprofessionalism. The disappointment in my friend’s voice was evident, and even his boss called me in to explain the situation. Convincing my friend to embrace the modern system and move away from Excel had been challenging, and now we had to redo the entire large invoice using Excel!
Identifying the Security Lapse
In the aftermath of the attack, I conducted a thorough analysis of how the attacker breached my system. The glaring oversight was having my PostgreSQL instance’s IP address exposed to the public on port 5432, making it vulnerable to attackers’ scanning scripts.
postgres://username:password@<external ip>:5432
However, the IP address was not the main issue. My lack of applying basic security by selecting a complex password made it simple for the attackers. It is embarrassing saying this as a Technology professional!
postgres://postgres:postgres@44.55.66.77:5432
The combination of both the exposed IP and simple credentials made it easy for a script cyber attacker to scan potentially thousands of PostgreSQL instances and guess the combination of username and password until a successful response is found. The attacker would focus on the successful ones and cause damage.
Conclusion
In my role as Technology Leader in my organization, this experience has served as that constant anchoring reminder of how important security is and what it can cost. It cost me a friend and his reputation of me which was a lot to me. For companies, it could cost millions and clients as well as irreversible reputational damage especially if you are in financial software.
One cannot be angry at the attacker. It is the reality and the way of the world today. Those threats will never go away. The responsibility lies with you. Every Technologist has the responsibility to understand security in their domain. We cannot offload it to security specialists anymore. Companies receive thousands of cyber attacks per day. Defensive programming and best practices on cloud integrations are critical to any system.

